
Por Mariana López
August 3, 2020
Contxto – What a week it must have been over at Mexican logistics startup, iVoy. When your users’ data has been potentially compromised, you have a lot to do.
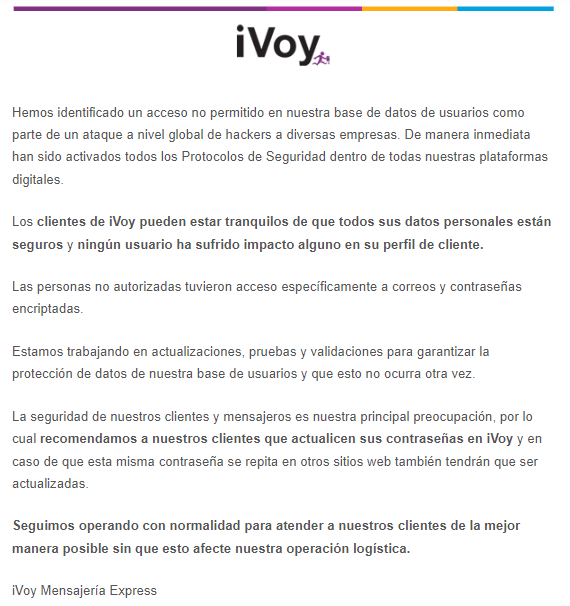
Last Tuesday (28), news broke that it was among a series of companies to experience a data breach. In the process, a reported 127,432 account users’ emails and iVoy passwords were exposed on an online forum.
Putting things in perspective: If a person uses the same password for everything (tsk tsk), that means they’re vulnerable on multiple fronts (e.g. email, social media, e-commerce platforms) when that password is obtained by an unauthorized party.
The startup stated that it’s deployed all its security protocols and that “users’ personal data is safe.” But just in case, it advised them to change their passwords.
It’s a daunting situation, but it’s always best to prepare beforehand, no matter your organization’s level of complexity.
One can only begin to fathom what goes through a Founder’s or CEO’s mind when they’re told there’s been a data breach. My guess is it’s a word that rhymes with “spit” or “firetruck.”
After which they must see to solving the problem.
This is an (extremely) oversimplified explanation, but it’s important you keep it in mind (if you haven’t done so already).
The first thing to do is assess the damage preferably with cybersecurity experts. What information was exposed, when, and so on. The measures you take will depend on the level of sensitivity of the data that was compromised.
Christmas wish lists and pictures of your dog won’t sound the alarm. Personal data (emails, phone numbers, banking info) call for all hands on deck.
Based on these findings, your team (preferably with legal counsel) will have to decide whether to disclose the breach to your users so they can protect themselves, as well as the relevant authorities.
In this case, iVoy issued a statement confirming the breach and advising its users on how to proceed.
You must also change your systems’ passwords and credentials and reevaluate your cybersecurity strategy.
If not, you might as well invite hackers through your digital door.
Throughout the aforementioned process, make sure you document everything.
If things go awry, you’ll need a paper trail to demonstrate that you did everything within your means to solve the problem and protect users’ information.
Will it be enough to shield you from a fine if worse comes to worst? Meh, it’s complicated.
It might save you in court (it depends, as usual). But the damage it does to your image can have long-lasting effects.
Related articles: Tech and startups from Mexico!
-ML

Por Yanin Alfaro
February 17, 2026

Por Israel Pantaleón
February 17, 2026

Por Stiven Cartagena
February 13, 2026