Por Carolina Zepeda
September 17, 2019
Contxto – Getting your cellphone, laptop or any device stolen can be extremely annoying and jeopardizing. Not only do you risk losing valuable items but also all of your private information. Thankfully, the Chilean startup Prey Project has created a platform to support people in safeguarding their data and technological items.
With Prey, it’s possible to get timely updates on where your devices, wherever they may be. Also, you can see firsthandidly if they’re connected to unknown networks or even block them and delete your info in case of theft.
When I first wrote this review, I asked a friend to take both my phone and laptop to test out Prey’s app. Fast forward two weeks and I actually ended up losing my phone while on my way to work. Honestly, I don’t even know how that happened. But it did.
Anyways, once I arrived at the office, I noticed it wasn’t in my bag and started freaking out. Fortuitously, I did not delete Prey from my phone after writing the review. It literally saved my life, so to speak.

Immediately I logged into Prey on my computer and reported the device as missing. I started sending messages, making the alarm sound and tracking its location. I also blocked it, of course.
Considering that I rewrote part of the review following the ordeal, you get to know the rest of the story.
“Prey is an open-source platform the prioritizes the clean and private handling of user data,” according to its website. The mission behind Prey is to provide the user with crucial evidence to retrieve what was lost or stolen. The platform does this by creating reports every two, ten or twenty minutes.
To get started, simply install Prey on your device. Download it on your phone through the PlayStore or Appstore. If you want to get Prey on your computer, you can obtain that directly through its website.
Once you download the software, you’ll be asked to create an account. Here is where you will manage all of your devices and mark them as lost, if necessary.

When a device is lost, the software will track its location and check any WiFi networks available in its surroundings. Additionally, pictures from all cameras are taken. This will allow the owner to know who is using the phone or laptop and maybe even catch a glimpse of where it is. After getting this information, a report will be created.
Users also have the ability to remain constantly vigilant over their property thanks to Prey’s online panel. Just log in and start taking preventative action.
Here, you can choose between different features that will notify you in case of theft, such as making an alarm sound, sending a message or blocking the device. You can even check the location and updated reports.
The first thing I did was download it on my phone. In order to operate, I had to allow the app to access my device. This way, blocking the phone and deleting all of its data remotely could be possible. Location and camera access should also be available to Prey for it to create security reports.
Contact and call access will permit Prey to permit the phone’s IMEI to send reports to you. Finally, Prey needs to be able to work over other apps. That way, you can 100 percent block your phone from being used or information getting compromised.
I know it sounds like a lot. Basically, it seems like you are giving Prey permission to take over your phone. The good news is, it’s for a good reason.
For my laptop, it was practically the same. After the download, I had to agree to give Prey access to a bunch of stuff like location, cameras, and control of my computer. It also created a mock report to show me how these will look like if it ever got stolen.
As I mentioned before, the first thing I did when I lost my phone was to track its location. As soon as I set the device as lost on the online panel, I got an email notifying me about that action. Immediately, Prey started tracking it and providing me with reports.
I have to say that the tracker worked perfectly. It gave me the exact location of where my phone was. I updated it a few times until the location stopped changing. When I went to pick it up, I wasn’t disappointed. Like serendipity, it was exactly where the app told me – a nearby office building.
Additionally, when checking the reports you can click on them and Prey will redirect you to Google Maps. There, you can check out the satellite view to have a better idea of where the device is.
Also in the report provided by Prey, I really could see all the WiFi networks surrounding it. Sad thing is, the platform did not take any picture with my phone’s camera. So that feature did not work for me.

Like I’ve already mentioned, there was no actual theft involved when I experimented with Prey over my laptop. I only asked a friend to take it to see how Prey worked.
Tracking a laptop gets a little bit trickier. Since it can’t be connected to WiFi the whole time, its harder to track. In that regard, the only way to get updates is if it gets connected to a network.
However, the security reports regarding this device do show pictures of whoever was using it. Most importantly, Prey took screenshots of what was being done on the computer. I could literally see all the documents that were open during its disappearance.
Before we dive deeper into all of the actions that Prey allows you to take, it’s important to know that these actions will only take place when the devices are connected to Prey Project’s servers. When does that happen? I have no idea.
When I first tried out the actions, the devices were wandering the streets with my friend. None of them actually worked until they were back with me. However, when I lost my phone for real, all actions functioned properly.
Anyways, the first action I took on both devices was to send a message.
A pre-written message will pop-up on your screen for your approval. If unlocked, you can also choose to make that message appear on the whole screen of the phone. Note that this is just a message, it will not actually lock the device until prompted.
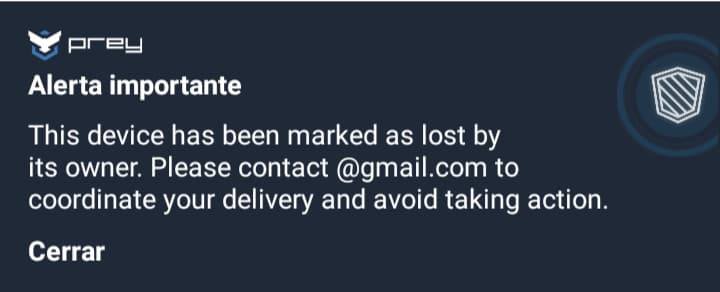
As soon as I had my cellphone back, I checked if the messages were still present. Lucky for me, they were. So, I can confirm that this feature works perfectly. Even though the phone received notifications, I never got an email from the person that took it.
On the other hand, when sending a message to my laptop, a small notification would appear in the middle of the screen. Personally, I thought it was pretty easy to simply move it away. Maybe if it took over the whole screen people would pay more attention to it.
The alarms are incredibly loud, which is certainly helpful. If your device is still nearby, this will definitely help you find it. There’s also the possibility to choose between three different sounds. I dare to say that these might even frighten off anybody that tries to steal it.
From what I recall, the sirens went off for around 30 seconds, but you can always replay them if needed. In case of missing computers, it doesn’t sound when the screen is down. Nevertheless, every time I opened it, it just wouldn’t be quiet. That was reassuring.
Thumbs up for this feature. I think it can really help users prevent their devices from getting stolen. Another good thing is if your device is simply misplaced, finding it will be pretty painless.
Obviously, I wasn’t near my phone when I set the alarms off when I couldn’t find it. But I do think they could’ve frightened the person into maybe giving it back.
When I was still looking for it, I asked my co-worker to call my number. When she did, nobody answered, which does not surprise me at all. But then somebody called my coworker back from an office building. Saying they had found the phone and wanted to give it back.
I find this a little hard to believe since the call came from a phone number we couldn’t call back. Secondly, this individual claimed to have found it somewhere I hadn’t been to that morning. Personally, it sounded kind of sketchy.
Probably one of the wisest things to do is immediately block your devices if they go missing. Luckily, Prey allows you to do this. Now in retrospect, I’m very glad to say that it worked seamlessly on my phone.
At first, with my phone, I thought nothing had actually happened. As soon as I unlocked it with my regular password, Prey had taken over my screen. I could do nothing but place the password I previously set when taking action over the panel.
When I tried it on my laptop, everything went smoothly, well kind of. Honestly, I got a little scared when Prey blocked my laptop.
Suddenly my whole screen went black. The only option I had was to write down Prey’s password. The thing is, my keyboard wasn’t working either. As much as I tried to type something, nothing happened.

It was not until I marked my device as found over the online panel that my keyboard started functioning again. Then I could type out the password with no problem at all. Needless to say, the blocking feature can be really effective but also a little daunting.
Prey Project is a freemium platform. This means that you can use it for free but if you want access to other cool features and actions, you’ll need a subscription.
For instance, with the free version, you can secure up to three devices. Whereas, by getting the Home package, you can protect ten devices.

Prey allows you to set up “control zones” for your devices. The only thing you need to do is write down an address and set up the range within the area where your device should be. Following suit, you can select to get an email every time a device leaves that designated area. Likewise, you can set up any of the actions that I previously mentioned.
Another option is to recover files remotely from your device by sending a download link to an email. Part of this entails the ability to delete all the information you want from your devices.
Here, users are able to establish actions on a schedule or condition. Depending on the circumstances, it will trigger an action.
Prey Project has special features for Android users. For example, Android owners can prevent anyone from deleting Prey from their device by creating a separate password. If you want to delete it, you’ll need to know the magic word.
Also, if anyone tries to shut down the phone, Prey will require a password to be entered as well. These perks definitely level up the security already provided by Prey.
I can definitely say that Prey exceeded my needs and expectations. After talking to whoever took the phone, I went to go get it back. In the end, it was in a nearby office building two blocks away from Contxto. The person that was supposed to have it never came down to meet me. Instead, she sent the device with a grumpy man.
Despite the unpleasant messenger, I’m grateful I got it back. In the process, I also got to try out Prey Project and everything the app offers. Overall, I can say I did enjoy the app and found it intuitively easy to use. The layout is simple and it doesn’t require much time to acclimate.
Nonetheless, I still can’t say why the reports didn’t include photos from the person that took the phone. Maybe it was the internet connection? Aside from that, I think Prey provides excellent services in patrolling the whereabouts of your devices. Without a doubt, I would encourage people to try this out!
Fun fact, Prey actually works with police authorities back in Chile! From the sounds of that, this proves that the app can certainly be effective. After all, one of the main perks over the app is the ability to obtain tangible evidence. As a result, filing theft reports can be extremely less complicated.
-CZ